
Everything needs maintenance, and Microsoft had planned automatic maintenance for the host machines responsible for hosting Azure Virtual Machines for some time. This would force Virtual Machines hosted in Azure to reboot and reallocate to newly maintained hosts. Virtual machines that where either off, or had been rebooted, was already done with this maintenance process. Only running VMs were remaining.
The maintenance window for North- and West Europe regions, was scheduled for 9.-12. of January 2018. Customers using Scale Sets and Availability Groups for their Azure Virtual Machines would've experienced no down time, but for those who wanted to manually control start time of this maintenance process, could do so any time before the scheduled maintenance window.
![]()
However, due to a recent announcement regarding some major vulnerabilities found in a lot of CPU's, not only from Intel, but some AMD and ARM, Microsoft forced the Azure VM Automated Maintenance to start around 03:00 o'clock this very Wednesday, 3. of January.
CPU's dated all the way back to 1995 could be vulnerable. The vulnerabilities were even OS independent (Windows, Linux, Unix, Android, iOS, Mac OS, BSD...), which makes this event one biggest, security wise, in recent time. An attack could be carried out through JavaScript, which also make everything with a web browser a potential target.
No wonder Microsoft had to patch up Azure. You can read more about the CPU vulnerabilities, named 'Spectre' and 'Meltdown', and what Microsoft has done to address the issue, here: Microsoft Blog - Securing Azure customers from CPU vulnerability
We at Ironstone first issued an informational email to our customers about the planned maintenance window, but had to counter with a new email with the new information we received, Thursday morning.
So, how does this affect you?
VMs hosted in Azure:
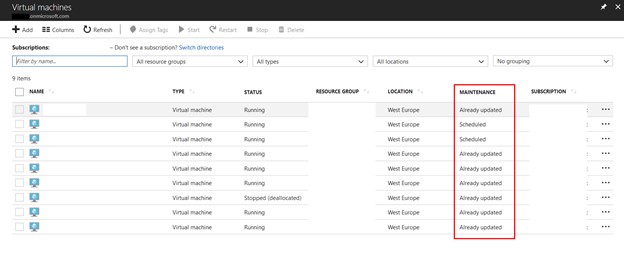
- If your VMs are already marked as 'maintained' within the Azure Portal > Virtual Machines, you are all good. Microsoft have also made patches for Windows OS itself, but if the host is maintained and patched, you are all good.
- If your VMs are marked as 'scheduled', you VMs are already in queue for the automated maintenance process.
Personal devices:
- These vulnerabilities affect everything from PCs, routers, cellphones and more. For an OS not virtualized on a patched host (everything but VMs really), make sure you are up to date, and look for keywords like 'cpu vulnerability', 'spectre' and 'meltdown' in recent changelogs.
- Also make sure browser and other programs are up to date. Mozilla has issued a fix to Firefox with version latest version 57.0.4.
Why this blog post?
We want to make sure we do our part in getting this important information out there.
![]()
Stay safe, and have a great weekend!
- The Ironstone Team